|
|
@@ -9,6 +9,8 @@
|
|
|
|
|
|
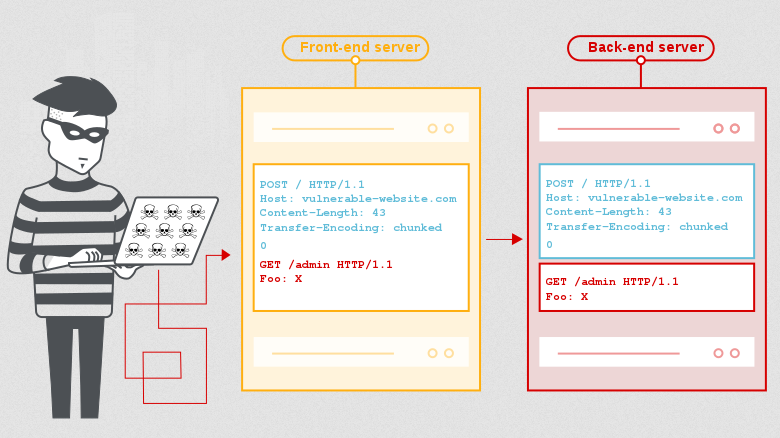
HTTP request smuggling is a technique for interfering with the way a web site processes sequences of HTTP requests that are received from one or more users.
|
|
|
|
|
|
+
|
|
|
+
|
|
|
Request smuggling vulnerabilities are often critical in nature, allowing an attacker to bypass security controls, gain unauthorized access to sensitive data, and directly compromise other application users.
|
|
|
|
|
|
#### Installing:
|
|
|
@@ -43,9 +45,9 @@
|
|
|
|
|
|
|
|
|
|
|
|
+
|
|
|
+
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
-
|
|
|
-
|